IDS stands for Intrusion Detection System. It is used to monitor traffic entering any network and helps in detecting malicious activity. It is important to note that IDS only detects malicious activities, and does not prevent attacks.
This article describes various techniques to evade IDS (Intrusion Detection System) and their implementation using the NMAP tool.
Organizations might have IDS in place to monitor network traffic before packets are routed to their internal networks. IDS employs various methods to detect suspicious activities:
- Anomaly-based
- Signature-based
- Host-based
- Network-based
Please refer to the article Intrusion Detection System (IDS) to know more about IDS.
Types of Evasion Techniques:
Like any other system, IDS have vulnerabilities that can be exploited by attackers to evade them.
1. Packet Fragmentation: In this technique, the IP packets are split into smaller fragments. By doing this, the TCP header is split across multiple fragments. When IDS encounter the packets, they enqueue them for checking any malicious activity. However, as the number of fragments increases, there is an increase in the CPU and network bandwidth consumption. For this reason, IDS ignores evaluating such packets. Hence, these fragments may pass undetected through the IDS.

The -f flag is used to create fragments. So the packet after the IP header is broken down into fragments of size 8 bytes or less. For example, if the size of the packet after the IP header is 10 bytes, then it will be split into two fragments of size 8 bytes and 2 bytes respectively. Specifying -f twice would create fragments of size 16 bytes. We can also specify our own size using -mtu flag. However, the size must be a multiple of 8. The fragments created using the above command can be captured using Wireshark.

The above picture shows frame 6125 sent to 127.0.0.1. The highlighted part shows that this frame was reassembled in IP frame 6127. Hence, we can conclude that frame 6125 was a part of frame 6127, and fragmentation was done successfully.
2. Source Routing: Packets pass through a number of routers before reaching the target host. Routers consult the routing table to pass the packet to the next hop. IDS are also put in place to monitor the network traffic. However, the route taken by the packets can be manipulated by the attacker. The attacker can make sure that the packets take a route that does not contain the IDS.
3. Source Port Manipulation: Sometimes IDS might allow network packets to pass without any inspection if they arrive at a particular port like port 80 which is primarily used for HTTP. This improper configuration can be exploited by attackers by manipulating the source port of packets. Hence, packets arriving at such ports can go unnoticed by the IDS.

The –source-port or -g flag can be used for specifying the source port of packets. The image below shows the packets sent as a result of executing the above command. We can see that the source port of all SYN packets is 22.

4. IP Address Decoy: The attacker sends packets to the target host by using the IP addresses of other hosts. So different packets have different IP addresses. Hence, it becomes difficult for the IDS to identify the actual IP address of the attacker. However, one of the packets has the actual IP address of the attacker, and if the IDS is configured to block traffic from all these IP addresses then the attacker cannot evade the IDS. This technique is used to scan ports at the target host. So an attacker can identify whether a particular port at the target host is running or not.
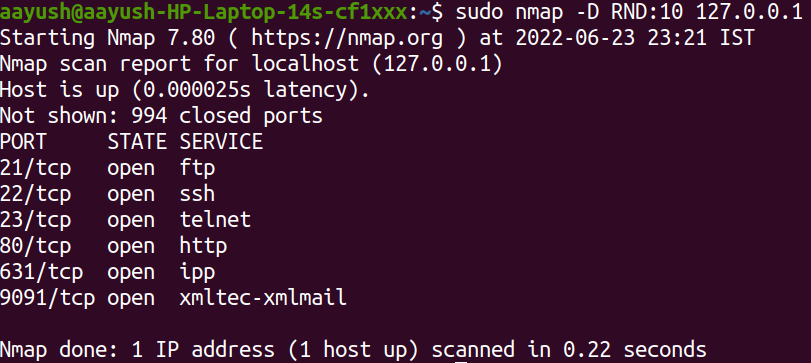
-D flag can be used for a decoy scan. RND option is used for generating random IP addresses. In the above example, 10 IP addresses were generated randomly and sent to the target host. We can see that packets were sent to the same target host from 10 different IP addresses including the actual IP address (127.0.0.1) of the attacker in the image below.

5. IP Address Spoofing: IP Address Spoofing simply means using some other machine’s IP address to send packets to the target host. Again, this technique can be used to scan ports which are usually done before the actual attack. So the IDS may identify the innocent hosts as malicious ones. However, using NMAP for performing IP address spoofing won’t produce useful results as the reply packets from the target host will be sent to the spoofed IP address. -S <ip-address> option can be used to perform IP address spoofing.

You can refer to the article IP Spoofing to know more.
6. Customizing Packets: IDS can be evaded by customizing the data packets. Customizing can be done by replacing data in the payload or appending data to the payload. Following are some ways to customize data-
(a) Unicode-based Evasion: Unicode is used to represent characters from different languages, emojis, etc. So, the payload can contain Unicode representation of data. However, a message having the same meaning could be represented using a different Unicode. By replacing data in the payload, malicious packets can pass through a signature-based IDS if the newly created pattern is not a part of the signature set stored.
(b) Appending binary data: This appends binary data to the payload. The data to be appended must be specified in hexadecimal.
nmap <target ip-address> --data 0xabcdefab
(c) Appending string: This appends a regular string to the payload.
nmap <target ip-address> --data-string "danger"
(d) Appending random data: This appends random data of specified length to the payload. Length can be anything between 0-65400. However, values greater than 1400 are not recommended as they could be greater than MTU.
nmap <target ip-address> --data-length <length>





 Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖
Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖