A session fixation attack is a type of remote code execution attack which is used to exploit software designed with the web-server Session Management feature. When a website is running an HTTP server, the server’s session state information can be stolen and then retrieved by an attacker to take over the browser or use it for further attacks. There are many tools that can help you detect session fixation attacks in your organization in order to prevent future attacks. A Session fixation attack is also known as Session Fixation Vulnerability (SFV).
In this article, we will see a session fixation attack and why it is important to secure it against attackers. Further, this article will discuss some frameworks and tools that can help you find those vulnerabilities in your system.
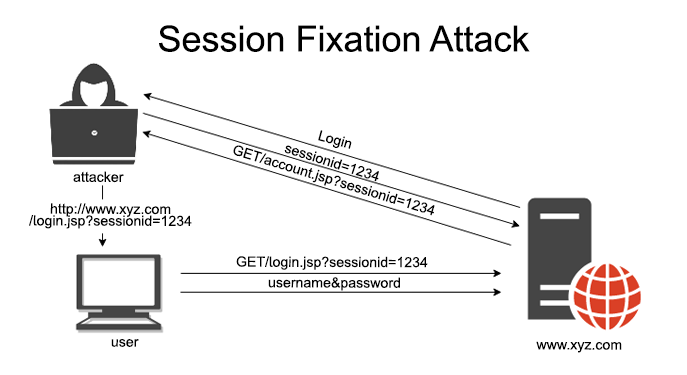
Session Fixation Attack:
- A Session fixation attack is an attack that occurs when a malicious user sets up a fake session before the legitimate users are able to log in. This leads to the entire system getting compromised and used to steal sensitive data.
- Session fixation attack is most commonly seen in banking systems, where hackers try to get access by setting up an account with minimum start-up requirements.
- With this method, they bypass any security measures, like CAPTCHA or fingerprint recognition, that banks might have implemented prior to stealing sensitive data. One of the methods used by banks against session fixation attacks is tokenization, which protects accounts while making it difficult for hackers to use fake credentials.
- A session fixation attack is a type of remote code execution attack which is used to exploit software designed with web-server session management features.
- When a website is running on an HTTP server, the server’s session state information can be stolen and then retrieved by an attacker to take over the browser or use it for further attacks.
Procedure:
- The attacker creates a malicious HTTP session with the victim’s browser, hijacks the client’s authentication, and copies the user.
- The attacker can do this by intercepting HTTP traffic from/to the browser, modifying or replaying existing valid sessions, or engineering a new malicious one. Session theft exploits vulnerabilities in applications that do not properly protect their data.
- The attacker then accesses and modifies data related to the captured session, such as cookies.
- HTTP protocol features like GET and POST methods provide a way for clients to send information to the server, but it does not contain a mechanism for clients to notify the server that this information has been received.
- To facilitate this exchange of information, HTTP supports Cookies. Since Cookies are sent back and forth between browser and server at every request/response cycle, we can also use them to hijack clients’ sessions with websites.
- Cookies can be used by attackers in order to employ session hijacking attacks, which is exactly what Session Hijacking or Session Fixation attacks are about. Session fixation techniques, such as cross-site scripting (XSS), cross-site request forgery (CSRF), and session stealing, are active threats that are already known in the wild.
Examples:
For example, in a session fixation attack, the hacker provides the server with his client’s session ID and is able to access any server he wants without the need for proper credentials.
This particular type of attack uses malicious scripts placed on websites to generate random ID sessions which aren’t compliant with security standards. Hackers can utilize front-end validation services but are able to bypass them. One way hackers do this is by analyzing browser cookies for other people who were already on-site at one point during their visit, as well as what sites users have recently been to in order to ensure that they can provide the website with a legitimate ID session in order to get around any front end validation service put into place.
Session fixation has been a common attack
vector for exploits that utilize the Java applet, which is a program
that runs within the user’s web browser. The hacker’s script is able to
detect when the user has left their browser, and can then re-establish a
new session with the server.
In order to avoid this type of attack
from taking place, users must always set Java security settings to
‘high’ to prevent this from happening. This basically means that all
applications on the user’s computer are required to be set up before
they will be allowed to run.
Conclusion:
There are several tools and frameworks you can use to detect Session Fixation attacks, but normally this kind of attack is detected by your security team or analysts. You need to be alert to invalid sessions and take measures to secure them against attacks. One of the most common ways is using Sessions Control page(s) or malicious scripts that detect whether a session is fixated or not.





 Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖
Hlo guys wellcome to our community its non profit community made for hackers
and we are helping people to know scam and fraud and developing new things of hacking to get up in digital world 🌎 so let’s start 🎖